Cypher Exploited - A Quick Look
Introduction
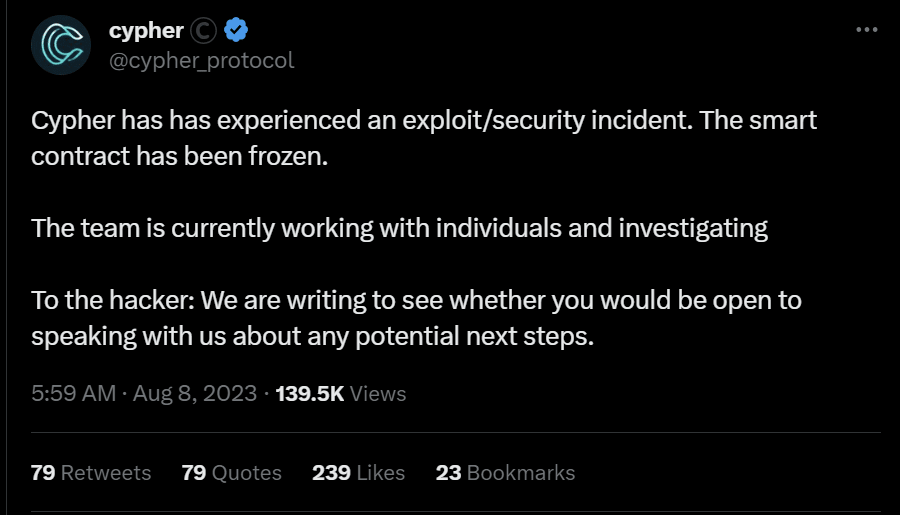
On Aug 7, 2:00 pm UTC, Cypher protocol tweeted about the exploit incident and had already frozen their smart contract.
In this analysis, we will take a quick look into the incident about the
- Hacker's wallet activity
- Exploited amount
- Cypher protocol activity in the last month
Tweet link: https://twitter.com/cypher_protocol/status/1688641036476731393
Methodology
- In this analysis, we will focus on the hacker's wallet
HHm4wK91XvL3hhEC4hQHo544rtvkaKohQPc59TvZeC71 - To calculate the exploited amount, we will use the current token price and exclude other actions that hackers take (the hacker's wallet had swapped several times)
- To find the Cypher activity in the last month, three contract addresses have been considered:
CYPHER3ziDd1rasgBcGGbx4fMtSS72x6NEM5Zvx2vNmKCYPHER79cJLzQ8iyyr6oeizfGgR9YU9NM9oTMPWak5oQCYPH3o83JX6jY6NkbproSpdmQ5VWJtxjfJ5P8veyYVu3
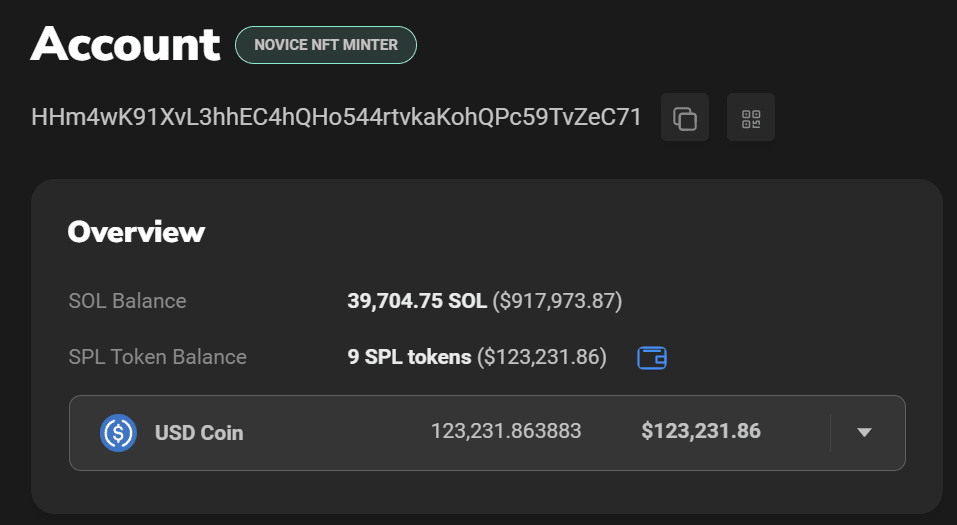
Unfortunately, there has been a total of $1.05m exploited from Cypher. Accounting from ~38k SOL or around $893k and 153k USDC.
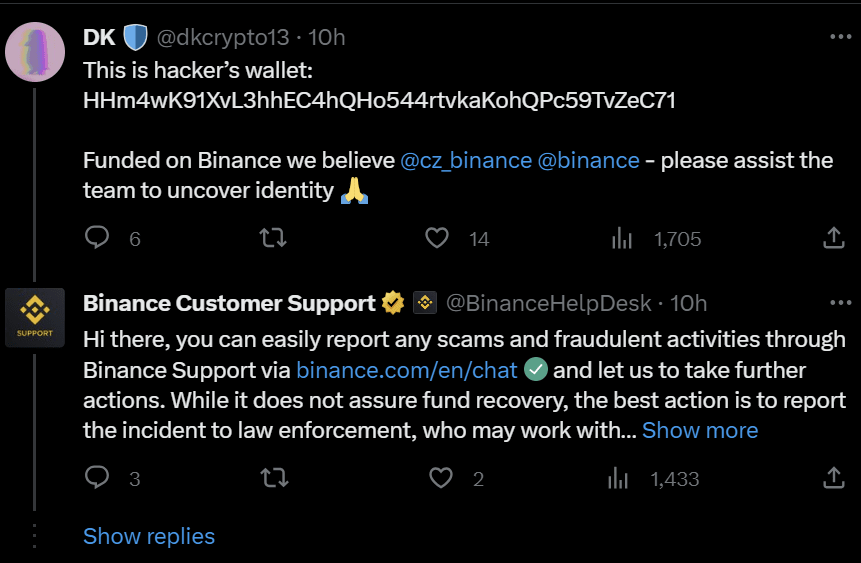
Interestingly, after the exploit, the hacker's wallet transferred 30,000 USDC to the Binance account.
Is this mean hacker is a Binance user?
In this section, we will look into Cypher's activity in the last month.
We can consider Cypher as one of the active protocols in Solana. There are 2.7m txs and 1,400 unique users since last month, or a daily average of 86k txs and 45 users, respectively.
The daily charts also indicate the popular tokens that users do with their transactions. We can see that USDC and SOL are the most popular token transferred in the Cypher protocol. Regrettably, both got exploited by the hacker.
The charts focus on the amount of transferred in Cypher by the token. We can see the peak on Aug 8th, the day that Cypher got exploited. More than $6m movement in volume, more than triple or quadruple compared with last week.
The bar chart also indicates the most popular token over the last month.
Almost $10m USDC has been transferred in and out of Cypher, followed by $6.6m of SOL, $4.4m of JitoSOL, and $4.35m of MSOL.
Conclusion
In this analysis, we looked into the Cypher incident.
Unfortunately, Cypher has been exploited for around one million USD, accounting for SOL (~85%) and USDC (14%).
The exploiter had transferred some of USDC to the Binance account ($30,000)
The remaining ~$950k remains in the address,
https://solscan.io/account/HHm4wK91XvL3hhEC4hQHo544rtvkaKohQPc59TvZeC71
Dashboard by: h4wk
Date: 8th August 2023
Discord: h4wk10
Twitter: https://twitter.com/h4wk10
Powered by: flipsidecrypto
What might come next?
The Cypher protocol already tries to contact the exploiter. However, the contact back hasn't been found.
We can hope that transferring USDC to a Binance account is an exploiter mistake since every Binance account can be tracked to find the actual user that is the owner of the account.